Privacy and Confidentiality
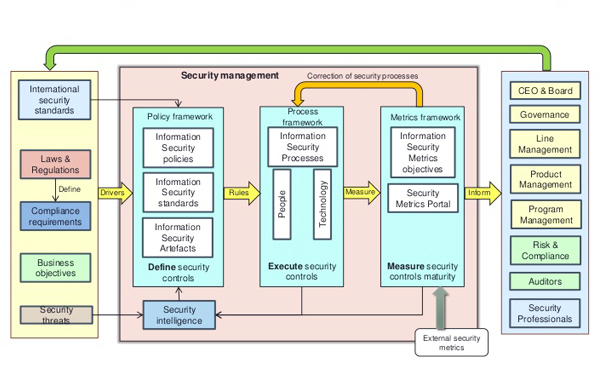
Oakridge takes security and confidentiality of client information very seriously and that is why we have implemented stringent security safeguards and processes for every information touch-point. Since our processes are clear and well-defined, we are able to immediately detect and handle any information breach and provide 360° security.
Our security process comprises of four stages: Planning, Protection, Detection, and Response. These four stages drill down to all security aspects related to People, Technology, Physical, and Network infrastructures.